Before understanding what is Risk Assessment and how to do Risk Assessment, we should get a clear understanding of what is Risk and its related terms according to ISO 27001.
The probability of an event that will have a negative effect is called “Risk”. The level of risk reflects: the likelihood of the unwanted event and the potential consequences of the unwanted event. And when the probability of an event results into a positive effect, it is termed as an “Opportunity”.
Evaluation of the possibility that a particular event or threat may damage on an organization is known as Risk Analysis. Risk assessment takes into account the likelihood that the event will occur, which can be evaluated quantitatively (e.g., as a percentage or frequency) or qualitatively (e.g., as low, medium, or high). The term “Event” refers to a particular incident or occurrence, like a system failure or security breach, that may result in different kinds of loss or harm. Organizations can enhance overall resilience and security by implementing suitable measures and controls to minimize possible damage and reduce the chance of events through an awareness of these risks and their probability-based management.
Organizations need to do risk analysis because it helps them to find out possible threats and weaknesses that could affect their business goals or operations. Organizations can prioritize risks and adopt efficient management methods and controls by evaluating risks according to their likelihood and impact. This proactive strategy can result in cost savings by preventing or minimizing future losses or damages. It also improves decision-making and standard compliance. Risk analysis plays is a crucial role to protect their resources, uphold their reputation, and guarantee long-term viability.
“Risk Assessment” is a thorough process of assessing potential risks that could impact an organization, project, or activity. It starts with identifying potential risks, threats and vulnerability and then carefully evaluating the risks associated with them, considering the likelihood of their occurrence and what the potential outcomes could be.
The objective is to develop appropriate strategies and actions to either prevent these risks from materializing or reduce their impact if they do occur with the help of Annex A controls listed in ISO 27001. The ultimate goal is to establish a systematic approach of comprehending and managing risks effectively, which in turn supports better decision-making, enhances safety measures, strengthens the organization’s security protocols ensuring continuous business operations.
Here is the process showing how to conduct a risk assessment:
- Prepare an Asset Register and share it with the clients. For more information/details on Asset Register and its format, click on the download button. Once you receive the details about the assets present in the organization, you can commence the risk assessment.
- Following this, prepare a risk assessment format that includes details such as the category of the asset, name of the asset, value of the asset, and other relevant information. For additional details on the risk register, you can download our Risk Register/Assessment Format given below.
- Using the details from the Asset Register, fill the details like the available assets in the organization—specifically, Hardware Assets, Hardcopy Assets, Software Assets, and Softcopy Assets—along with their corresponding asset values in the designated columns of the Risk Register.
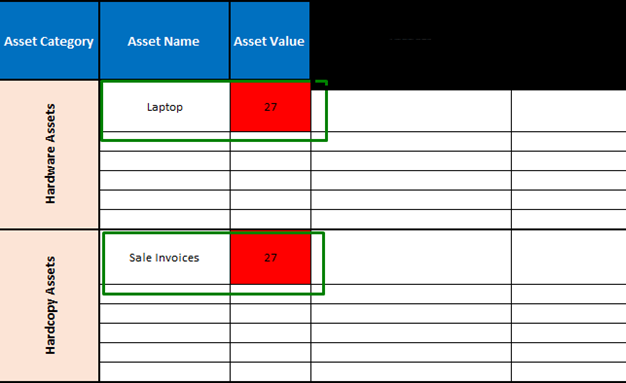
Figure 1 Risk Register: Highlighting the exemplary values for asset name and asset value under the groups of Hardcopy and Hardware Assets.
- With the help of the Master List of Threats and Vulnerabilities, write the associated threats and vulnerabilities for the listed assets in the risk register.
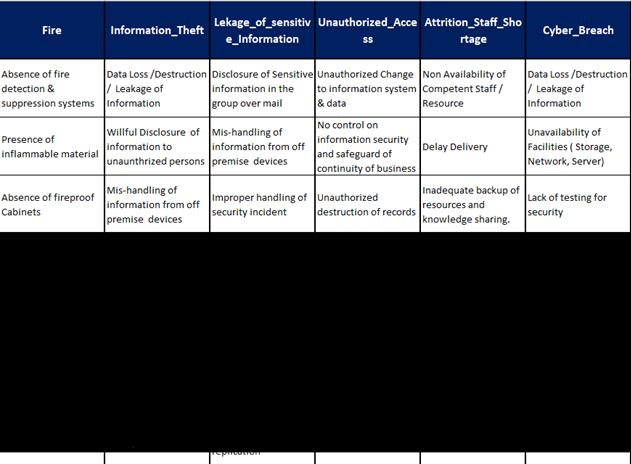
Figure 2 Master List Of Threats And Vulnerabilities (MLTV)
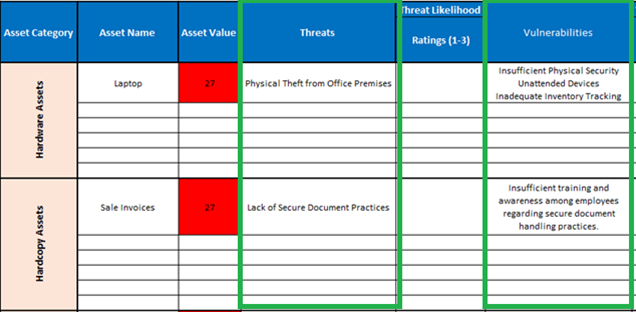
Figure 3 Risk Register: Highlighting the listed Threats and Vulnerabilities using MLTV
- After evaluating the risks associated with specified assets in Risk Register, assign a Threat Likelihood Rating. This rating, ranging from 1 to 3, will be based on the probability of the threat occurring. A rating of 1 indicates a low likelihood, 2 signifies a moderate likelihood, and 3 represents a high likelihood of occurrence.
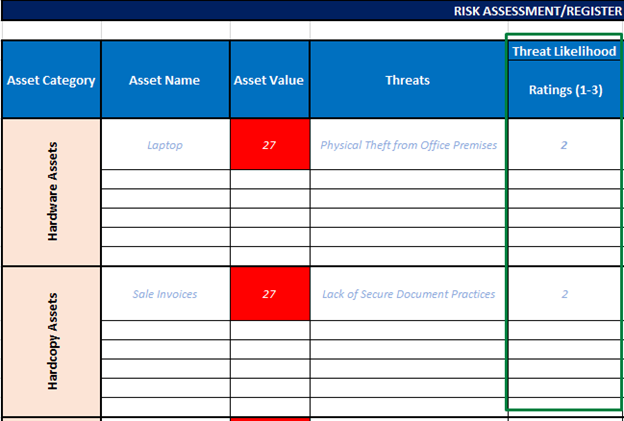
Figure 4 Risk Register: Highlighting Threat Likelihood Rating
- Having determined the likelihood of the threat, the next step involves assessing the severity of the vulnerability and assigning a Vulnerability Severity Rating. This requires a thorough analysis of the potential impact on the associated asset and the degree to which it could adversely affect the company or business. A rating of 1 defines a low severity of vulnerability, 2 signifies a moderate severity of vulnerability, and 3 represents a high of vulnerability.
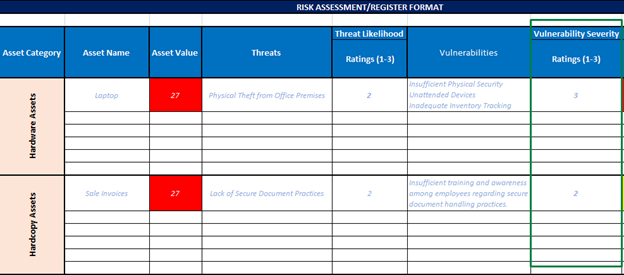
Figure 5 Risk Register: Highlighting Vulnerability Rating
- The concluding task involves assigning a risk rating to the assets enumerated in the risk register, calculated using the following formula: Risk Rating = (Asset Value * Threat Likelihood * Vulnerability Severity) / 243 * 100. Subsequently, the risk ratings are may categorized as follows: For example - values between 1-30 signify Low Risk (Green), values between 31-60 indicate Medium Risk (Yellow), and values between 61-100 denote High Risk (Red).
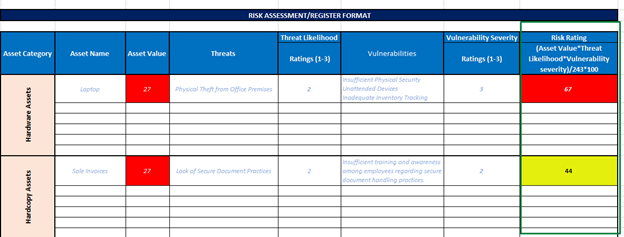
Figure 6 Risk Register: Highlighting Risk Rating
- Note : The shown images are some of the glimpses of the Risk Register, for more details you can download our Risk Register Format.
For more such informtion on ISO 27001 related topics follow us on –

